[PPML] Add Azure Attestation part to Attestation Basic Docs (#6781)
* Init * Fix * Refine * Refine * Refine
This commit is contained in:
parent
c87c01bd8d
commit
bd112d6cf3
1 changed files with 13 additions and 3 deletions
|
|
@ -35,7 +35,7 @@ The basic workflow of attestation:
|
|||
```
|
||||
|
||||
The key steps in attestation:
|
||||
* Quote Generation. Generate a Quote/Evidence with SDK/API. This quote is signed by a pre-defined key, and it cannot be modified. You can add 128b its user data into a SGX quote.
|
||||
* Quote Generation. Generate a Quote/Evidence with SDK/API. This quote is signed by a pre-defined key, and it cannot be modified. You can add 128bits user data into a SGX quote.
|
||||
* Quote Verification. Verify a Quote/Evidence with SDK/API.
|
||||
|
||||
### Attestation in E2E PPML applications
|
||||
|
|
@ -69,12 +69,22 @@ When working with an attestation service, we can define a policy/requirement for
|
|||
|
||||
With this attestation service design, we can avoid adding malicious applications or modules to distributed applications.
|
||||
|
||||
#### Attestation Service for Cloud Service Provider (CSP)
|
||||
#### Attestation Service from Cloud Service Provider (CSP)
|
||||
|
||||
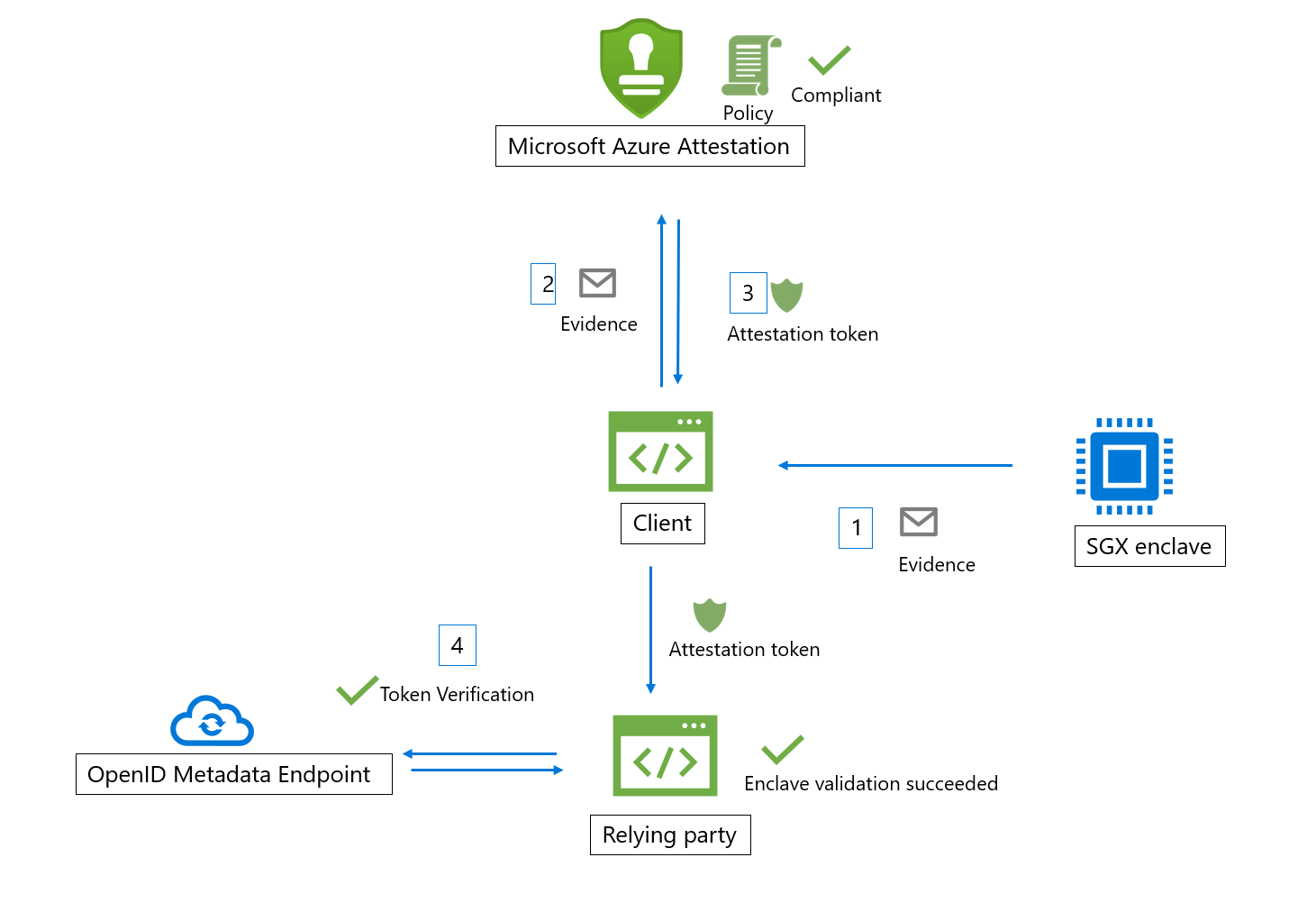
Azure provides an Attestation Service for applications running in TEE VM or containers provided by Azure. Before we submit our applications to a cloud service, we need to verify the identity and security posture of the platform. Azure Attestation receives evidence from the platform, validates it with security standards, evaluates it against configurable policies, and produces an attestation token for claims-based applications.
|
||||
|
||||
The involved actors in Azure Attestation workflow:
|
||||
* Relying party: The component which relies on Azure Attestation to verify enclave validity.
|
||||
* Client: The component which collects information from an enclave and sends requests to Azure Attestation.
|
||||
* Azure Attestation: The component which accepts enclave evidence from client, validates it and returns attestation token to the client
|
||||
|
||||
|
||||
|
||||
Here are the general steps in a typical SGX enclave attestation workflow (using Azure Attestation): The client collect the evidence from the enclave by generating a quote and send it to an URI which refers to an instance of Azure Attestation. Azure Attestation validates the submitted information and evaluates it against a configured policy. If the verification succeeds, Azure Attestation issues an attestation token and returns it to the client. The client sends the attestation token to relying party. The relying party calls public key metadata endpoint of Azure Attestation to retrieve signing certificates. The relying party then verifies the signature of the attestation token and ensures the enclave trustworthiness.
|
||||
|
||||
### Advanced Usage
|
||||
|
||||
During remote attestation, the attestation protocol will build a secure channel. It can help build [TLS connection with integirty](https://arxiv.org/pdf/1801.05863.pdf). Meanwhile, attestation can be [integrated with HTTP protocol to provide trusted end-to-end web service](https://arxiv.org/abs/2205.01052).
|
||||
During remote attestation, the attestation protocol will build a secure channel. It can help build [TLS connection with integrity](https://arxiv.org/pdf/1801.05863.pdf). Meanwhile, attestation can be [integrated with HTTP protocol to provide trusted end-to-end web service](https://arxiv.org/abs/2205.01052).
|
||||
|
||||
### References
|
||||
|
||||
|
|
|
|||
Loading…
Reference in a new issue